By Mark Antalik
In Part One of this two-part data breach triage series, we discussed identifying, understanding and communicating during a breach situation and how breaches should be managed. In this article, we will elaborate on perpetuation through digital forensics, as well as outline approaches to notification and identity monitoring. As discussed in Part One of this series, a well-designed breach response program that addresses the steps noted below will minimize the negative impact on both short and long-term business goals.
Steps Addressed in Part One of Article Series:
Steps Addressed in Part Two of Article Series
Let’s discuss perpetuation, and notification and identity monitoring in detail.
Perpetuation
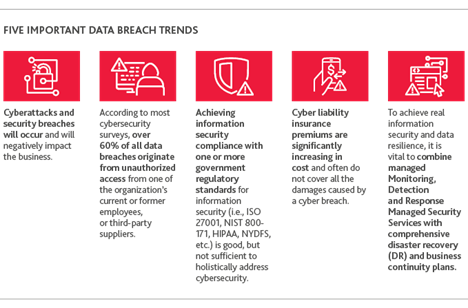
Preservation of key information and evidence during and after a breach is vital to understanding the nature and scope of the incident. Organizations that actively deploy endpoint and network monitoring are better positioned to identify suspicious activity and contain the breach. Organizations that are not currently deploying such technology and processes are not only at greater risk of breach, but will find it more difficult to understand the nature and scope of the breach should one occur.
Many organizations already employ threat intelligence technology and teams to understand and mitigate data risk. However, once an incident occurs, cyber forensics teams need to dig deeper into the incident including gathering technical clues and indicators of the compromise. Gathering this data will help to identify both the nature and scope of the breach.
Understanding the nature of the breach is important so the breach can be contained and measures can be implemented to prevent similar attacks in the future. From a technical perspective, this may involve analyzing IP addresses, file names and hash values to inform further data investigations. The goal is to identify operational details about the motivation of the threat actors; uncover the tools, techniques and procedures used to infiltrate the system or environment; and gain strategic intelligence to evaluate the overarching risks associated with the incident.
As the cyber forensics team is gathering information about the nature of the breach, it needs to simultaneously identify the scope of the beach. Understanding what data may have been accessed or exfiltrated is often not an exact science. There are many technical layers and, only when combined with knowledge of the nature of the breach, can the potentially exfiltrated dataset truly be assessed. Organizations must collect, analyze and correlate both the data and the facts. Knowledge of the entire potentially exfiltrated dataset is critical to informing the required disclosures and notifications and to determining the scope and risk of intellectual property and other sensitive data loss.
As discussed in Part One of the article series, having a plan in place prior to the breach will provide explicit guidance for response resources, reduce emotional conflicts in tense breach situations, and demonstrate to clients, donors, and volunteers that your organization is in control of the situation and is concerned about protecting personal information. Having a business continuity plan provides situational awareness and decision‑making support during the chaos of a crisis to get your organization back up and running as quickly as possible.
Notification and Identity Monitoring
There are several types of breach‑related notifications. Compliance‑related notifications include notifications to state, federal and global regulators; notifications to impacted entities and individuals; and notifications to roles such as the organization’s Data Protection Officer. Other notifications may include law enforcement, the board, stockholders, business partners and company executives – the degree to which these notifications occur will depend on the organization and the nature and/or scope of the breach.
From a jurisdictional regulatory impact perspective, consider building a map to visualize the exposure, plotting impacted entities and individuals (based on the information learned while investigating the nature and scope of the breach) to determine if there are any concentrations of impact that would suggest prioritizing notifications in particular jurisdictions. Domestic organizations are often surprised that they maintain data for individuals in the European Union, Asia Pacific or Latin America regions and identifying and visualizing this exposure can accelerate the notification process given how fast breach response situations move.
As the master notification list is being compiled, organizations need to identify notification letter requirements. Considerations include grouping notification content by region and data categories, defining the necessary notification letter template elements, identifying language/translation needs, determining call center and credit monitoring logistics and determining distribution method(s) for the notifications. An important aspect of notification is establishing a regulatory metrics report. The report documents jurisdictions, number and type of notifications, response rates and any exceptions identified during the process. These reports are critical to demonstrate regulatory due diligence and tracking through the notification process.
Depending on the scope of the breach, a call center may be required to address stakeholder questions and issues, and comply with regulations. Call centers should be staffed with trained professionals with experience protecting sensitive data. Call center staff should follow defined data handling procedures to maintain the security of any personal information logged during call center interactions. Consider developing training kits including scripts and FAQs. Consider call center logistics, physical security, local language requirements, staff management and scale. Consider the potential importance of industry experience for call center operators, potential to deploy offshore options and tracking of key performance indicators. Data breach call centers are typically established and maintained for 12‑18 months following the incident. To mitigate the number of complaints to regulators, establish procedures to address and diffuse escalated situations.
Be prepared for additional breach requirements related to individual and consumer rights afforded by data protection regulations such as the European Union’s General Data Protection Regulation (GDPR), the California Consumer Privacy Act (CCPA) and the Virginia Consumer Data Protection Act (CDPA). In summary, and not exhaustive, these regulations empower individuals to make requests such as a request to delete the individual’s data, show the individual what data the organization stores about them or request that the organization correct the individual’s data if there are inaccuracies. Under these regulations, organizations typically have 30 – 45 days (differs by regulation) to fulfill these requests. Many other states and global jurisdictions are in the process of enacting individual rights requirements beyond typical breach response obligations.
Individual rights requests often spike after a data incident, from a few per month, to potentially hundreds or thousands post breach. Right‑sizing and scaling a process to address these individual rights can be challenging. Processes need to be set up to address the intake of the requests, verification that the individual is who they purport to be, coordination of the requests, research to identify the information requested, consolidation of data/information into template responses, review and dissemination of the data or information back to the individual and tracking every step in the process. Depending on the size and complexity of the organization, the individual rights response process can be resource intensive and time consuming. Consider exploring and deploying data protection software that can help automate parts of the individual rights request process.
Depending on the nature and scope of the breach, having a team to support the investigation into lost identity or impacted credit may be required. Identity monitoring services must be able to investigate compromised sensitive data like Social Security numbers, country IDs and medical information, while monitoring for personally identifiable information and protected health information on the dark web. Qualified fraud examiners can assist with restoring credit and applying appropriate protections moving forward. For instances requiring organizations to provide individuals with access to credit reports, along with individual credit monitoring tools, it is also important to have experienced professionals that are licensed to investigate credit issues.
As noted in Part One of this article series, a breach can be a real test of resiliency. Organizations must plan for a breach and be clear and transparent to clients, donors, volunteers and other third parties about how the organization collects, uses, stores, shares, protects and disposes of sensitive and personal data. Organizations who meet the crisis head on may be able to emerge stronger, be better prepared for the next incident and build a closer connection with their constituencies.
Copyright © 2021 BDO USA, LLP. All rights reserved. www.bdo.com